The simplest way to generate a key pair is to run ssh-keygen without arguments. In this case, it will prompt for the file in which to store keys. Here's an example: klar (11:39) ssh-keygen Generating public/private rsa key pair. Oct 22, 2019 A better solution would be to share the same set of SSH keys between Windows and WSL so that you have one set of keys for one machine. Setup SSH on Windows first. My recommendation is that you set up SSH on the Windows side first. Follow the instructions over on Github’s documentation to do this. It will walk you through generating the key. Launch Bash on Ubuntu on Windows from the start menu and make sure SSH is installed by entering following command at the command prompt: sudo apt install ssh The key generation process is identical to the process on a native Linux or Ubuntu installation. You can use the ssh-keygen command line utility to create RSA and DSA keys for public key authentication, to edit properties of existing keys, and to convert file formats. When no options are specified, ssh-keygen generates a 2048-bit RSA key pair and queries you for a key name and a passphrase to protect the private key.
How to Generate an SSH key in Windows 10
As you may already know, Windows 10 includes built-in SSH software - both a client and a server! This feature is available in the OS starting in version 1803. When the client option is installed, we can use it to generate a new SSH key.
RECOMMENDED: Click here to fix Windows errors and optimize system performance
Generate Ssh Key Windows Command Line Code
On Windows machines, the freeware open-source software PuTTY is the de-facto standard when it comes to SSH and Telnet. With Windows 10, Microsoft has finally listened to its users after years of them requesting an SSH client and server. By including an OpenSSH implementation, the value of the OS increases.The provided SSH client is similar to the Linux client. At first glance, it appears to support the same features as its *NIX counterpart. It is a console app, so you should be able to start it from the command prompt.
To proceed, you need to enable the OpenSSH Client feature. Check out the following text:
Assuming that you have it installed, you can do the following.
For Monster Hunter Generations Ultimate on the Nintendo Switch, a GameFAQs message board topic titled 'Summarized list for Key Quests'. 
To Generate an SSH key in Windows 10,
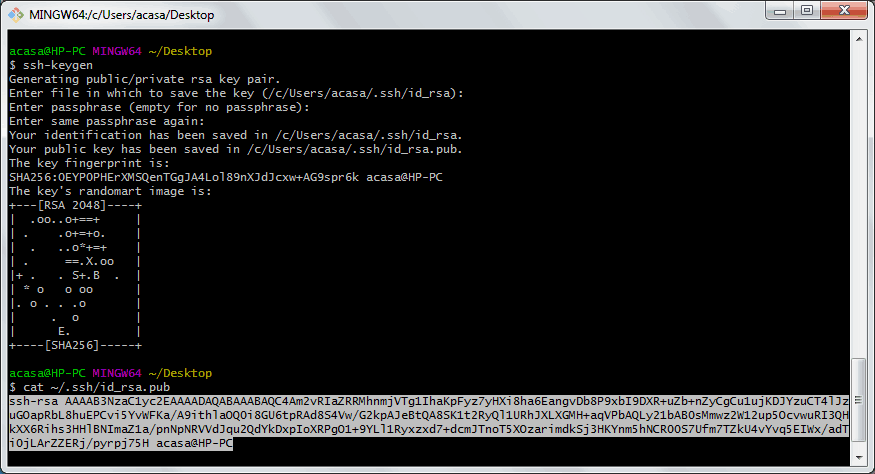
- Open a new command prompt.
- Type
ssh-keygenand hit the Enter key. - The app will ask for the save location, offering
C:usersyour user name.sshid_rsaby default. - Next, you will be prompted to enter a passphrase. You can just hit the Enter key to skip it.
- Finally, you will see the fingerprint for your key and SHA256. The default algorithm is RSA 2048.
You are done. Your public key will be saved to the id_rsa.pub file, by default it is C:usersyour user name.sshid_rsa.pub. You can now upload this file to the target machine you want to access with SSH. Do not share your private SSH key (id_rsa) unless you know what you are doing!
SSH supports a number of other public key algorithms using with keys, such as:
- rsa - this is a classic algorithm based on the difficulty of factoring large numbers. Recommended keys size - 2048 or above.
- dsa - yet another legacy algorithm based on the difficulty of computing discrete logarithms. It is no longer recommended.
- ecdsa - a new Digital Signature Algorithm standarized by the US government, using elliptic curves. It supports 256, 384, and 521 key sizes.
- ed25519 - this algorithm is the latest options included in OpenSSH. Certain software lacks support for it.
You can specify the algorithm using the -t option and change the key size using the -b switch. Some examples:
That's it.
Also, see the following articles:
RECOMMENDED: Click here to fix Windows errors and optimize system performance
Overview
Public key authentication is a way of logging into an SSH/SFTP account using a cryptographic key rather than a password.
If you use very strong SSH/SFTP passwords, your accounts are already safe from brute force attacks. However, using public key authentication provides many benefits when working with multiple developers. For example, with SSH keys you can
- allow multiple developers to log in as the same system user without having to share a single password between them;
- revoke a single developer's access without revoking access by other developers; and
- make it easier for a single developer to log in to many accounts without needing to manage many different passwords.
How Public Key Authentication Works
Keys come in pairs of a public key and a private key. Each key pair is unique, and the two keys work together.
These two keys have a very special and beautiful mathematical property: if you have the private key, you can prove you have it without showing what it is. It's like proving you know a password without having to show someone the password.
Public key authentication works like this:
- Generate a key pair.
- Give someone (or a server) the public key.
- Later, anytime you want to authenticate, the person (or the server) asks you to prove you have the private key that corresponds to the public key.
- You prove you have the private key.
You don't have to do the math or implement the key exchange yourself. The SSH server and client programs take care of this for you.
Generate an SSH Key Pair
You should generate your key pair on your laptop, not on your server. All Mac and Linux systems include a command called ssh-keygen that will generate a new key pair.
If you're using Windows, you can generate the keys on your server. Just remember to copy your keys to your laptop and delete your private key from the server after you've generated it.
To generate an SSH key pair, run the command ssh-keygen.
It will look like this when you run it:
You'll be prompted to choose the location to store the keys. The default location is good unless you already have a key. Press Enter to choose the default location.
Next, you'll be asked to choose a password. Using a password means a password will be required to use the private key. It's a good idea to use a password on your private key.
After you choose a password, your public and private keys will be generated. There will be two different files. The one named id_rsa is your private key. The one named id_rsa.pub is your public key.
You'll also be shown a fingerprint and 'visual fingerprint' of your key. You do not need to save these.
Configure an SSH/SFTP User for Your Key
Method 1: Using ssh-copy-id
Generate Ssh Key Windows Command Line 10
Now that you have an SSH key pair, you're ready to configure your app's system user so you can SSH or SFTP in using your private key.
To copy your public key to your server, run the following command. Be sure to replace 'x.x.x.x' with your server's IP address and SYSUSER with the name of the the system user your app belongs to.
Method 2: Manual Configuration
If you don't have the ssh-copy-id command (for example, if you are using Windows), you can instead SSH in to your server and manually create the .ssh/authorized_keys file so it contains your public key.
First, run the following commands to make create the file with the correct permissions.
Next, edit the file .ssh/authorized_keys using your preferred editor. Copy and paste your id_rsa.pub file into the file.
Log In Using Your Private Key
You can now SSH or SFTP into your server using your private key. From the command line, you can use:
If you didn't create your key in the default location, you'll need to specify the location:
If you're using a Windows SSH client, such as PuTTy, look in the configuration settings to specify the path to your private key.
Granting Access to Multiple Keys
The .ssh/authorized_keys file you created above uses a very simple format: it can contain many keys as long as you put one key on each line in the file.
If you have multiple keys (for example, one on each of your laptops) or multiple developers you need to grant access to, just follow the same instructions above using ssh-copy-id or manually editing the file to paste in additional keys, one on each line.
When you're done, the .ssh/authorized_keys file will look something like this (don't copy this, use your own public keys):
Additional Information
Retrieve Your Public Key from Your Private Key
The following command will retrieve the public key from a private key:
The next-generation network (NGN) is a body of key architectural changes in telecommunication core and access networks.The general idea behind the NGN is that one network transports all information and services (voice, data, and all sorts of media such as video) by encapsulating these into IP packets, similar to those used on the Internet.NGNs are commonly built around the Internet Protocol. Key idea behind next generation technology. Mar 31, 2020 The World Economic Forum is an independent international organization committed to improving the state of the world by engaging business, political, academic and other leaders of society to shape global, regional and industry agendas. Incorporated as a not-for-profit foundation in 1971, and headquartered in Geneva, Switzerland, the Forum is tied to no political, partisan or national interests.
This can be useful, for example, if your server provider generated your SSH key for you and you were only able to download the private key portion of the key pair.
Note that you cannot retrieve the private key if you only have the public key.
Correcting Permissions on the .ssh Directory
The instructions in this article will create your server's .ssh directory and .ssh/authorized_keys file with the correct permissions. However, if you've created them yourself and need to fix permissions, you can run the following commands on your server while SSH'd in as your app's system user.
Disabling Password Authentication
NOTE: When changing anything about the way SSH is accessed(ports, authentication methods, et cetera), it is very strongly recommended to leave an active root SSH session open until everything is working as intended. This ensures you have a way to revert changes in the event something goes wrongand logins are not working properly.
As an extra security precaution, once you have set up SSH keys, you may wish to disable password authentication entirely. This will mean no users will be able to log into SSH or SFTP without SSH keys. Anyone entering a password will receive a message like:
Or:
Disabling password authentication is an excellent way to improve server security. Please see our guide here for the steps to accomplish this goal.
Then, test whether you're able to log in with a password by opening a new SSH or SFTP session to the server. Passwords should not be able to be used and, if everything has been done correctly, an error will be issued when someone tries to use a password. Unless this setting is changed back to allow password authentication, no users will be able to log in without an SSH key set up.