- Gpg Generate Key Command Line Online
- Gpg Generate Key Command Line Download
- Gpg Generate Key Command Line Code
- Gpg Command Line Options
- Gpg Generate Key Command Line In Excel
- Gpg Export Public Key Command Line
- Gpg Generate Key Command Line Free
- Generate Gpg Key Windows Command Line
Oct 03, 2019 Find out how to create and export a GPG keypair from the macOS command line. If you want to create a new key with more information, you should issue the command: gpg -full-generate-key. Jun 30, 2018 Create Your Public/Private Key Pair and Revocation Certificate. Use gpg -full-gen-key command to generate your key pair. Gpg -full-gen-key. It asks you what kind of key you want. Notice there’re four options. The default is to create a RSA public/private key pair and also a RSA signing key. Let’s hit Enter to select the default.
Related
Introduction
GPG, or GNU Privacy Guard, is a public key cryptography implementation. This allows for the secure transmission of information between parties and can be used to verify that the origin of a message is genuine.
In this guide, we will discuss how GPG works and how to implement it. We will be using an Ubuntu 16.04 server for this demonstration, but will include instructions for other distributions as well.
How Public Key Encryption Works
A problem that many users face is how to communicate securely and validate the identity of the party they are talking to. Many schemes that attempt to answer this question require, at least at some point, the transfer of a password or other identifying credentials, over an insecure medium.
Ensure That Only the Intended Party Can Read
To get around this issue, GPG relies on a security concept known as public key encryption. The idea is that you can split the encrypting and decrypting stages of the transmission into two separate pieces. That way, you can freely distribute the encrypting portion, as long as you secure the decrypting portion.
This would allow for a one-way message transfer that can be created and encrypted by anyone, but only be decrypted by the designated user (the one with the private decrypting key). If both of the parties create public/private key pairs and give each other their public encrypting keys, they can both encrypt messages to each other.
So in this scenario, each party has their own private key and the other user’s public key.
Validate the Identity of the Sender
Another benefit of this system is that the sender of a message can “sign” the message with their private key. The public key that the receiver has can be used to verify that the signature is actually being sent by the indicated user.
Set Up GPG Keys
GPG is installed by default in most distributions.
If for any reason GPG is not installed, on Ubuntu and Debian, you can update the local repo index and install it by typing:
On CentOS, you can install GPG by typing:
May 08, 2017 StarCraft II: Wings of Liberty Serial Key Download Code Crack key generator Full Game Torrent skidrow Origin Key and Steam Online Code Avaiable. StarCraft II: Wings of Liberty Serial Key Cd Key Free Download Crack Full Game StarCraft II: Wings of Liberty Serial Cd Key Generator License Activator Product Origin Keys Full Game Download Free. Aug 13, 2013 Starcraft 2: Wings of Liberty Cd-Key Generator + CRACK Battle between all races begin: Terrans, Protoss and Zergs are ready to fight. Wings of liberty key generator. Don’t forget to read instructions after installation. Enjoy Starcraft II Wings of Liberty Keygen And Crack (CD KEYS FREE). All files are uploaded by users like you, we can’t guarantee that Starcraft II Wings of Liberty Keygen And Crack (CD KEYS FREE) are up to date.
To begin using GPG to encrypt your communications, you need to create a key pair. You can do this by issuing the following command:
This will take you through a few questions that will configure your keys:
- Please select what kind of key you want: (1) RSA and RSA (default)
- What keysize do you want? 4096
- Key is valid for? 1y (expires after 1 year. If you are just testing, you may want to create a short-lived key the first time by using a number like “3” instead.)
- Is this correct? y
- Real name: your real name here
- Email address: your_email@address.com
- Comment: Optional comment that will be visible in your signature
- Change (N)ame, ©omment, (E)mail or (O)kay/(Q)uit? O
- Enter passphrase: Enter a secure passphrase here (upper & lower case, digits, symbols)
At this point, gpg will generate the keys using entropy. Entropy describes the amount of unpredictability and nondeterminism that exists in a system. GPG needs this entropy to generate a secure set of keys.

This process may take a long time depending on how active your system is and the keysize you selected. To generate additional entropy more easily, you can use a tool called haveged. Open up a new terminal and SSH into the server again to set up haveged on your server.
Create a Revocation Certificate
You need to have a way of invalidating your key pair in case there is a security breach or in case you lose your secret key. There is an easy way of doing this with the GPG software.
This should be done as soon as you make the key pair, not when you need it. This revocation key must be generated ahead of time and kept in a secure, separate location in case your computer is compromised or inoperable. To generate a revocation key, type:
You will be asked to confirm the revocation key creation and then prompted for the reason that it is being revoked. This information will be visible to other users if the revocation is used in the future. You can choose any of the available options, but since this is being done ahead of time, you won’t have the specifics. Often, it is a good idea to create a revocation certificate for each of the likely scenarios for maximum flexibility.
Afterwards, you will then be asked to supply a comment and finally, to confirm the selections. Before creating the revocation certificate, you will need to enter your GPG key’s passphrase to confirm your identity. The revocation certificate will be written to the file specified by the --output flag (revocation.crt in our example):
You should immediately restrict the permissions on the generated certificate file in order to prevent unauthorized access:
The revocation certificate must be kept secure so that other users cannot revoke your key. As the message states, you should consider backing the certificate up to other machines and printing it out, as long as you can secure it properly.
How To Import Other Users’ Public Keys
GPG would be pretty useless if you could not accept other public keys from people you wished to communicate with.
You can import someone’s public key in a variety of ways. If you’ve obtained a public key from someone in a text file, GPG can import it with the following command:
There is also the possibility that the person you are wishing to communicate with has uploaded their key to a public key server. These key servers are used to house people’s public keys from all over the world.
A popular key server that syncs its information with a variety of other servers is the MIT public key server. You can search for people by their name or email address by going here in your web browser:
You can also search the key server from within GPG by typing the following:
You can use this method of searching by name or email address. You can import keys that you find by following the prompts.
How To Verify and Sign Keys
While you can freely distribute your generated public key file and people can use this to contact you in a secure way, it is important to be able to trust that the key belongs to who you think it does during the initial public key transmission.
Verify the Other Person’s Identity
How do you know that the person giving you the public key is who they say they are? In some cases, this may be simple. You may be sitting right next to the person with your laptops both open and exchanging keys. This should be a pretty secure way of identifying that you are receiving the correct, legitimate key.
But there are many other circumstances where such personal contact is not possible. You may not know the other party personally, or you may be separated by physical distance. If you never want to communicate over insecure channels, verification of the public key could be problematic.
Luckily, instead of verifying the entire public keys of both parties, you can simply compare the “fingerprint” derived from these keys. This will give you a reasonable assurance that you both are using the same public key information.
You can get the fingerprint of a public key by typing:
This will produce a much more manageable string of numbers to compare. You can compare this string with the person themselves, or with someone else who has access to that person.
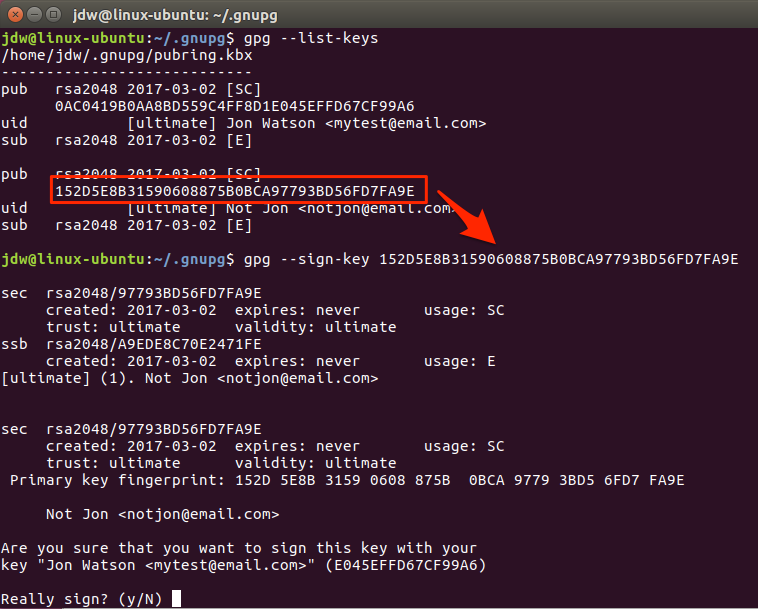
Sign Their Key
Signing a key tells your software that you trust the key that you have been provided with and that you have verified that it is associated with the person in question.
To sign a key that you’ve imported, simply type:
When you sign the key, it means you verify that you trust the person is who they claim to be. This can help other people decide whether to trust that person too. If someone trusts you, and they see that you’ve signed this person’s key, they may be more likely to trust their identity too.
You should allow the person whose key you are signing to take advantage of your trusted relationship by sending them back the signed key. You can do this by typing:
You’ll have to type in your passphrase again. Afterwards, their public key, signed by you, will be displayed. Send them this, so that they can benefit from gaining your “stamp of approval” when interacting with others.
When they receive this new, signed key, they can import it, adding the signing information you’ve generated into their GPG database. They can do this by typing:
They can now demonstrate to other people that you trust that their identity is correct.
How To Make Your Public Key Highly Available
Because of the way that public key encryption is designed, there is not anything malicious that can happen if unknown people have your public key.
With this in mind, it may be beneficial to make your public key publicly available. People can then find your information to send you messages securely from your very first interaction.
You can send anyone your public key by requesting it from the GPG system:
You can then send this file to the other party over an appropriate medium.
If you want to publish your key to a key server, you can do it manually through the forms available on most of the server sites.
Another option is to do this through the GPG interface. Look up your key ID by typing:
The highlighted portion in the output below is the key ID (look for the pub along the left-hand column if you’re uncertain about which one to use). It is a short way to reference the key to the internal software.
To upload your key to a certain key server, you can then use this syntax:
The key will be uploaded to the specified server. Afterwards, it will likely be distributed to other key servers around the world.
Encrypt and Decrypt Messages with GPG
You can easily encrypt and decrypt messages after you have shared your keys with the other party.
Encrypt Messages
You can encrypt messages using the “–encrypt” flag for GPG. The basic syntax would be:
This encrypts the message using the recipient’s public key, signs it with your own private key to guarantee that it is coming from you, and outputs the message in a text format instead of raw bytes. The filename will be the same as the input filename, but with an .asc extension.
You should include a second “-r” recipient with your own email address if you want to be able to read the encrypted message. This is because the message will be encrypted with each person’s public key, and will only be able to be decrypted with the associated private key.
So if it was only encrypted with the other party’s public key, you would not be able to view the message again, unless you somehow obtained their private key. Adding yourself as a second recipient encrypts the message two separate times, one for each recipient.
Decrypt Messages
When you receive a message, simply call GPG on the message file:
The software will prompt you as necessary.
If instead of a file, you have the message as a raw text stream, you can copy and paste it after typing gpg without any arguments. You can press “CTRL-D” to signify the end of the message and GPG will decrypt it for you.
Key Maintenance
There are a number of procedures that you may need to use on a regular basis to manage your key database.
To list your available GPG keys that you have from other people, you can issue this command:
Your key information can become outdated if you are relying on information pulled from public key servers. You do not want to be relying on revoked keys, because that would mean you are trusting potentially compromised keys.
You can update the key information by issuing:
This will fetch new information from the key servers.
You can pull information from a specific key server by using:
Gpg Generate Key Command Line Online
You may receive error messages if any of your keys cannot be found on the key server.
Conclusion
Using GPG correctly can help you secure your communications with different people. This is extremely helpful, especially when dealing with sensitive information, but also when dealing with regular, everyday messaging.
Because of the way that certain encrypted communications can be flagged by monitoring programs, it is recommended to use encryption for everything, not just “secret” data. That will make it more difficult for people to know when you are sending important data or just sending a friendly hello.
Previous: The quick key manipulation interface, Up: Unattended Usage of GPG [Contents][Index]
4.5.4 Unattended key generation
The command --generate-key may be used along with the option--batch for unattended key generation. This is the mostflexible way of generating keys, but it is also the most complex one.Consider using the quick key manipulation interface described in theprevious subsection “The quick key manipulation interface”.
The parameters for the key are either read from stdin or given as afile on the command line. The format of the parameter file is asfollows:
- Text only, line length is limited to about 1000 characters.
- UTF-8 encoding must be used to specify non-ASCII characters.
- Empty lines are ignored.
- Leading and trailing white space is ignored.
- A hash sign as the first non white space character indicates a comment line.
- Control statements are indicated by a leading percent sign, the arguments are separated by white space from the keyword.
- Parameters are specified by a keyword, followed by a colon. Arguments are separated by white space.
- The first parameter must be ‘Key-Type’; control statements may be placed anywhere.
- The order of the parameters does not matter except for ‘Key-Type’ which must be the first parameter. The parameters are only used for the generated keyblock (primary and subkeys); parameters from previous sets are not used. Some syntactically checks may be performed.
- Key generation takes place when either the end of the parameter file is reached, the next ‘Key-Type’ parameter is encountered or at the control statement ‘%commit’ is encountered.
Gpg Generate Key Command Line Download
Control statements:
Print text as diagnostic.
Suppress actual key generation (useful for syntax checking).
Perform the key generation. Note that an implicit commit is done atthe next Key-Type parameter.
Do not write the key to the default or commandline given keyring butto filename. This must be given before the first commit to takeplace, duplicate specification of the same filename is ignored, thelast filename before a commit is used. The filename is used until anew filename is used (at commit points) and all keys are written tothat file. If a new filename is given, this file is created (andoverwrites an existing one).
Gpg Generate Key Command Line Code
See the previous subsection “Ephemeral home directories” for a morerobust way to contain side-effects.
This option is a no-op for GnuPG 2.1 and later.
See the previous subsection “Ephemeral home directories”.
This option is a no-op for GnuPG 2.1 and later.
Using this option allows the creation of keys without any passphraseprotection. This option is mainly intended for regression tests.
If given the keys are created using a faster and a somewhat lesssecure random number generator. This option may be used for keyswhich are only used for a short time and do not require fullcryptographic strength. It takes only effect if used together withthe control statement ‘%no-protection’.
General Parameters:
Starts a new parameter block by giving the type of the primarykey. The algorithm must be capable of signing. This is a requiredparameter. algo may either be an OpenPGP algorithm number or astring with the algorithm name. The special value ‘default’ maybe used for algo to create the default key type; in this case a‘Key-Usage’ shall not be given and ‘default’ also be usedfor ‘Subkey-Type’.
The requested length of the generated key in bits. The default isreturned by running the command ‘gpg --gpgconf-list’.
This is optional and used to generate a CSR or certificate for analready existing key. Key-Length will be ignored when given.
Space or comma delimited list of key usages. Allowed values are‘encrypt’, ‘sign’, and ‘auth’. This is used togenerate the key flags. Please make sure that the algorithm iscapable of this usage. Note that OpenPGP requires that all primarykeys are capable of certification, so no matter what usage is givenhere, the ‘cert’ flag will be on. If no ‘Key-Usage’ isspecified and the ‘Key-Type’ is not ‘default’, all allowedusages for that particular algorithm are used; if it is not given but‘default’ is used the usage will be ‘sign’.
Gpg Command Line Options
This generates a secondary key (subkey). Currently only one subkeycan be handled. See also ‘Key-Type’ above.
Length of the secondary key (subkey) in bits. The default is returnedby running the command ‘gpg --gpgconf-list’.
Key usage lists for a subkey; similar to ‘Key-Usage’.
If you want to specify a passphrase for the secret key, enter it here.Default is to use the Pinentry dialog to ask for a passphrase.
Gpg Generate Key Command Line In Excel
The three parts of a user name. Remember to use UTF-8 encoding here.If you don’t give any of them, no user ID is created.
Set the expiration date for the key (and the subkey). It may eitherbe entered in ISO date format (e.g. '20000815T145012') or as number ofdays, weeks, month or years after the creation date. The specialnotation 'seconds=N' is also allowed to specify a number of secondssince creation. Without a letter days are assumed. Note that thereis no check done on the overflow of the type used by OpenPGP fortimestamps. Thus you better make sure that the given value makesense. Although OpenPGP works with time intervals, GnuPG uses anabsolute value internally and thus the last year we can represent is2105.
Set the creation date of the key as stored in the key information andwhich is also part of the fingerprint calculation. Either a date like'1986-04-26' or a full timestamp like '19860426T042640' may be used.The time is considered to be UTC. The special notation 'seconds=N'may be used to directly specify a the number of seconds since Epoch(Unix time). If it is not given the current time is used.
Gpg Export Public Key Command Line
Set the cipher, hash, and compression preference values for this key.This expects the same type of string as the sub-command ‘setpref’in the --edit-key menu.
Add a designated revoker to the generated key. Algo is the public keyalgorithm of the designated revoker (i.e. RSA=1, DSA=17, etc.)fpr is the fingerprint of the designated revoker. The optional‘sensitive’ flag marks the designated revoker as sensitiveinformation. Only v4 keys may be designated revokers.
This is an optional parameter that specifies the preferred keyserverURL for the key.
This is an optional parameter only used with the status linesKEY_CREATED and KEY_NOT_CREATED. string may be up to 100characters and should not contain spaces. It is useful for batch keygeneration to associate a key parameter block with a status line.
Gpg Generate Key Command Line Free
Here is an example on how to create a key in an ephemeral home directory:
If you want to create a key with the default algorithms you would usethese parameters:
Generate Gpg Key Windows Command Line
Previous: The quick key manipulation interface, Up: Unattended Usage of GPG [Contents][Index]